A Step-by-Step Roadmap to Achieving SOC 2 Compliance
For growing businesses, especially in technology and SaaS, demonstrating trust is non-negotiable. Clients want assurance that their data is safe, processes are reliable, and systems are resilient. That’s where SOC 2 compliance comes in.
SOC 2, developed by the American Institute of Certified Public Accountants (AICPA), is an auditing framework that evaluates whether a company has the right controls in place to protect customer data. Achieving SOC 2 isn’t just about passing an audit — it’s about building credibility, strengthening security practices, and unlocking new business opportunities.
If your company is starting this journey, here’s a step-by-step roadmap to SOC 2 compliance.
Step 1: Understand the SOC 2 Framework
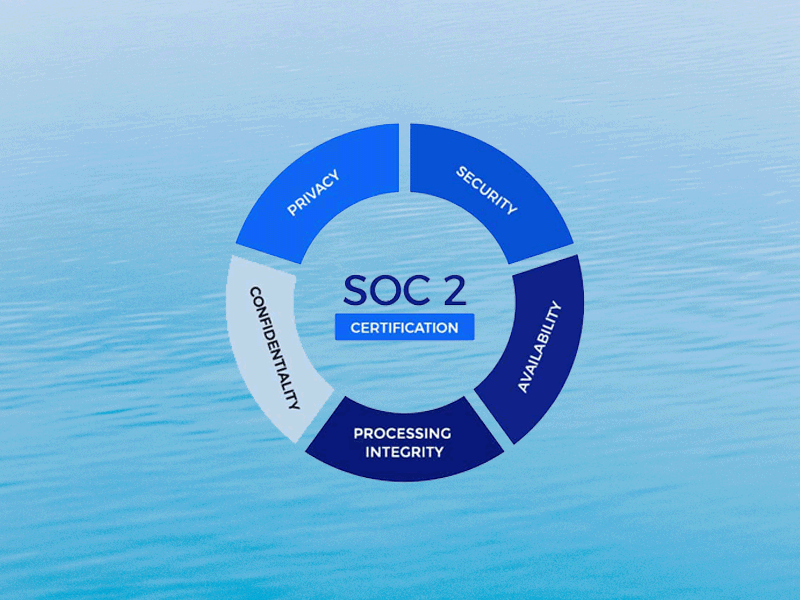
Before diving in, it’s important to understand what SOC 2 entails. The framework is based on the five trust service principles:
- Security (the foundation of every audit)
- Availability
- Processing Integrity
- Confidentiality
- Privacy
Your business won’t necessarily be audited against all five — only the ones relevant to your services. For example, a SaaS platform may focus on security, availability, and confidentiality, while a payroll processor may include processing integrity and privacy.
Why this step matters: Understanding the principles ensures your compliance efforts align with the unique risks and expectations of your industry and clients.
Step 2: Choose Between SOC 2 Type I and Type II
SOC 2 reports come in two forms:
- Type I evaluates your systems and controls at a single point in time.
- Type II assesses the effectiveness of those controls over a longer period, typically 6–12 months.
Type I is a good starting point if you’re new to compliance and want to show clients your policies exist. Type II offers greater credibility since it proves your controls actually work in practice.
Why this step matters: Many enterprise clients specifically require a Type II report before signing contracts, making it essential for winning larger deals.
Step 3: Conduct a Readiness Assessment
A readiness assessment (sometimes called a gap analysis) helps identify where your current practices fall short of SOC 2 requirements. This stage involves reviewing existing policies, access controls, monitoring systems, and documentation.
Key outcomes of a readiness assessment:
- A clear picture of compliance gaps
- A prioritized roadmap for remediation
- Reduced risk of delays during the formal audit
Why this step matters: Going into an audit unprepared can result in failure, wasted resources, and damaged credibility. A readiness assessment saves time and money by fixing issues early.
Step 4: Implement Necessary Controls and Policies
Based on the readiness results, you’ll need to address gaps in your security and compliance practices. This could involve:
- Enforcing multi-factor authentication for system access
- Drafting or updating policies around incident response, data retention, and vendor management
- Setting up centralized monitoring and logging tools
- Training employees on security awareness
Why this step matters: SOC 2 isn’t just about technology — it’s about people, processes, and governance. Well-documented policies backed by real enforcement prove your company takes security seriously.
Step 5: Select a CPA Firm for the Audit
Only licensed CPA firms can perform SOC 2 audits. Choosing the right auditor is crucial — they should understand your industry, your company size, and the specific risks you face. Some firms specialize in startups and SaaS companies, while others cater to large enterprises.
Why this step matters: An experienced auditor makes the process smoother, provides practical guidance, and delivers a report that your clients will trust.
Step 6: Undergo the Audit
During the audit, the CPA firm will review your controls, test their effectiveness (for Type II), and evaluate how well your organization aligns with the trust service principles.
What to expect:
- Interviews with staff
- Evidence collection (e.g., policy documents, system logs, access records)
- Testing of technical and operational controls
Why this step matters: This is the official step where your organization earns its SOC 2 report, which becomes a powerful tool in client negotiations and sales cycles.
Step 7: Review and Address Findings
If the auditor identifies issues, you’ll receive recommendations for remediation. Addressing these quickly not only strengthens your security posture but also demonstrates your commitment to continuous improvement.
Why this step matters: SOC 2 isn’t about perfection — it’s about accountability. Even with minor findings, clients will value your transparency and progress.
Step 8: Maintain Ongoing Compliance
SOC 2 is not a one-and-done process. To maintain compliance, businesses must continually monitor systems, update policies, and train employees. Annual audits or continuous monitoring tools can help ensure your controls remain effective.
Why this step matters: Customers expect ongoing proof of security, not a one-time certificate. Continuous compliance builds long-term trust and keeps you ahead of evolving threats.
Final Thoughts
SOC 2 compliance may feel complex, but when broken into steps, the path becomes much clearer. From understanding the framework and choosing the right report type to preparing with a readiness assessment and maintaining ongoing compliance, each stage builds a stronger foundation of trust and security.
In today’s business landscape, SOC 2 is more than an audit — it’s a growth enabler. It helps you close enterprise deals, reduce risk, and position your company as a reliable, security-conscious partner.
By following this roadmap, your organization won’t just pass an audit — you’ll create a culture of accountability and resilience that supports long-term success. Polimity can offer assistance with your compliance needs.